In today’s increasingly digital world, email has become a primary tool for communication among professionals, businesses, and online services. However, at the same time, “Phishing Emails” or fraudulent emails have been rising at an alarming rate. The goal of these emails is to trick users into revealing sensitive information such as passwords, credit card numbers, or personal data, often disguised to look completely legitimate.
Understanding what a Phishing Email is and how to spot one is important for everyone. Even with strong security systems in organizations or email platforms, phishing scams often exploit the recipient’s trust to deceive them. In this article, BullVPN will help you stay aware of phishing emails, recognize which ones are real or fake, and know what to do if you accidentally click a suspicious link.
What is a Phishing Email?
A phishing email is a fraudulent message made to look like it comes from a trusted source such as a bank, e-commerce platform, or government agency. Its main purpose is to trick victims into revealing personal information by clicking links or entering data on fake websites.
Phishing emails often imitate real logos, fonts, or layouts so convincingly that recipients believe they are genuine. They may include messages like “Verify your account” or “Update your information urgently” designed to create panic and push users to respond without thinking.
Why is it a cybersecurity threat?
Because this type of email is one of the easiest yet most effective attack methods in the world of cybersecurity threats. Email phishing can cause corporate data breaches, system hacks, or financial losses in an instant. Malicious actors may sell the stolen information on the dark web or use it to launch further attacks in other forms.

Warning signs of a phishing email
1. The sender’s email address looks suspicious or almost identical to the real one
Instead of coming from “@email.com,” it appears as “@emai1.com.” In this example, the number 1 is used in place of the letter l, which at a quick glance can make the email look normal.
2. Messages that urge you to respond immediately
Techniques scammers use in phishing emails to pressure recipients into clicking links or replying without verifying the truth. Examples include “Your account will be suspended within 24 hours” or “Please verify your information today.” These messages rely on fear and urgency to trick users into disclosing sensitive information such as OTPs or credit card numbers without realizing it. If you receive an email like this, stay calm, check the sender’s domain, and avoid clicking any attached links.
3. Unknown links or attachments
These are elements in an email that lead to fake websites or files containing malware. Clicking or opening them can install harmful programs, steal passwords, or allow hackers to access sensitive data. Watch out for unexpected attachments with risky extensions (.exe, .scr, .js, .zip containing executable files, etc.) or links that show strange or mismatched URLs when you hover over them. If you encounter these, do not click or open them. Instead, check the URL by hovering your mouse, verify the sender through another channel (such as a phone call or official website), and if you already clicked, immediately disconnect from the internet, change all related passwords, scan for viruses, and inform your IT department or bank if needed.
4. Informal language or frequent spelling errors
Informal language or frequent spelling errors can indicate that an email may be a phishing attempt. Legitimate emails from real organizations usually use formal, accurate, and consistent language. In contrast, fake emails often contain odd wording, machine translations, grammar mistakes, or inappropriate phrases such as “Click now” or “Please click this link immediately to avoid account suspension.” If the message looks unprofessional or the language seems off, it’s best to assume it could be a phishing email and avoid replying or clicking any links.
5. Direct requests for personal information
One of the key warning signs of a phishing email is a direct request for sensitive information such as passwords, credit card numbers, OTP codes, or personal details via email or embedded links. Trusted organizations will never ask for confidential data through email. If you receive such a message, stop responding immediately, avoid clicking any links, and do not fill out any forms. Instead, contact the organization or company through official channels such as their verified website or phone number. If you’ve already shared your information, change your passwords, enable two-factor authentication (2FA), notify your bank or IT department, and run a malware scan right away.
Comparison between real emails and phishing emails
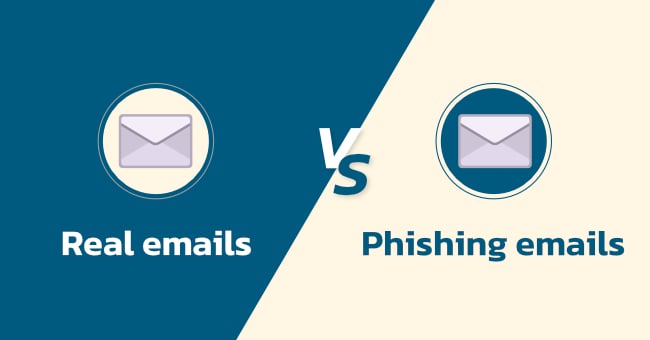
Example of a real email
-
The sender uses an official domain email.
-
No personal information is requested.
-
All links lead to HTTPS websites with domains matching the organization.
-
The language is formal and includes complete contact information.
Example of a phishing email and key warning signs
- The sender’s name looks similar but not identical, such as [email protected].
- Uses logos and urgent messages to prompt immediate action.
- Contains attachments like .zip or .exe files.
- Uses unusual language or contains spelling errors.
Key differences
- Real emails focus on user security.
- Phishing emails try to rush users into clicking quickly.
- Small details like the domain, links, or tone of the message make all the difference.
How to protect yourself and what to do when you receive a suspicious email
When you receive a suspicious-looking email, the most important thing is not to click right away. Always take time to verify it carefully. Start by checking the sender’s name and email domain to see if they match the legitimate organization. Then, hover your mouse over any links (without clicking) to check whether the destination leads to an official and trusted website.
If you notice spelling mistakes or suspicious domains, avoid them immediately. Do not open attachments unless necessary, especially those with extensions like .exe, .zip, .js, or .scr, as they may contain hidden malware.
In addition, you should enable Two-Factor Authentication (2FA) to enhance account security, change your passwords regularly, and keep your antivirus software up to date. Using a VPN is another effective way to encrypt your data and prevent hackers from intercepting information while you’re connected to the internet, especially when using public Wi-Fi. This helps keep you safe from email-based attacks in every situation.
Phishing Email Summary: How to Spot It and Stay Safe
Phishing emails are one of the most common cyber threats that often start with user carelessness. Being aware and double-checking before clicking any link is the best first line of defense. While technology can filter out many suspicious emails, no system is 100% secure if users are not cautious. To enhance your online safety, BullVPN helps encrypt your data and Hide IP Address, protecting you from data interception and reducing the risk of phishing emails that target users through insecure networks.